Securing network devices and servers over unsecured networks can pose a serious challenge for organizations. Luckily, the Secure Shell protocol, or SSH, has emerged as a popular network protocol for securely managing network devices and servers. SSH tunneling, also known as SSH port forwarding, is one effective method of transporting arbitrary network data securely over an SSH connection. In this article, we will explore the concept of SSH tunneling, its benefits, types, everyday use cases, and best practices to ensure safe and efficient use.
The Benefits of SSH Tunneling:
SSH tunneling has numerous advantages, and some of them are:
– Security: SSH tunneling ensures that data transmitted over the network remains encrypted and cannot be intercepted or tampered with by unauthorized users. Sensitive data can be transmitted over unsecured networks securely.
– Flexibility: SSH tunneling allows users to forward any type of network traffic through a single SSH connection, simplifying network management and reducing the number of open ports on your system.
– Interoperability: SSH is compatible with numerous operating systems and platforms, making it easy to establish secure connections between different systems.
Types of SSH Tunnels:
SSH tunnels come in three main types, and they are:
– Local Port Forwarding: This tunnel forwards a local port on the client system to a remote server. It’s useful for accessing remote services securely.
– Remote Port Forwarding: In this case, a remote port on the server is forwarded to a local port on the client system. This is useful for providing secure access to local services to remote users.
– Dynamic Port Forwarding: This type of tunnel creates a dynamic SOCKS proxy, allowing users to route arbitrary network traffic through the tunnel. This is especially useful for bypassing firewalls and content restrictions.
How SSH Tunneling Works:
Establishing an SSH tunnel requires an SSH client and server. The client initiates the connection to the server, and the server authenticates the client using public key authentication or password-based authentication. Once the connection is established, data can be securely transmitted through the tunnel.
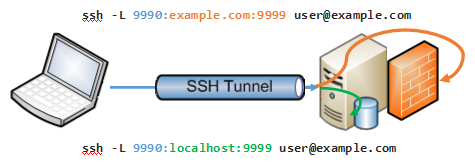
Local Port Forwarding:
Local port forwarding involves the client listening on a specified local port and forwarding any incoming traffic to a remote address and port via the SSH tunnel. This is useful for securely accessing remote services from a local machine.
Remote Port Forwarding:
Remote port forwarding is the opposite of local port forwarding, whereby the server listens on a specified remote port and forwards incoming traffic to a local address and port on the client system through the SSH tunnel. This allows remote users to access local services on the client machine securely.
Dynamic Port Forwarding:
Dynamic port forwarding creates a dynamic SOCKS proxy on the client machine, allowing users to route arbitrary network traffic through the SSH tunnel. It’s particularly useful for bypassing firewalls, content restrictions, or accessing resources on remote networks.
Everyday Use Cases for SSH Tunneling:
SSH tunneling has numerous use cases, and some of them are:
– Secure File Transfer: SSH tunneling is useful for safe and secure file transfers over the network, preventing unauthorized access or interception of data.
– Remote System Administration: With SSH tunneling, network administrators can remotely manage servers and network devices with ease, without worrying about data being intercepted or compromised.
– Secure Database Access: SSH tunneling comes in handy when accessing remote database servers securely. This prevents data from being tampered with or intercepted by unauthorized users.
– Bypassing Firewalls and Content Restrictions: SSH tunneling allows users to bypass firewalls, content restrictions, or access resources on remote networks securely.
Best Practices for SSH Tunneling:
Here are some best practices for using SSH tunneling to enhance security and efficiency:
– Key Management and Authentication: Use secure authentication methods like public key authentication instead of password-based authentication. Also, ensure that your SSH keys are properly managed and kept safe.
– Monitoring and Logging: Keep a record of all SSH tunneling activities through proper monitoring and logging mechanisms to detect any suspicious activities and prevent security breaches.
Conclusion:
SSH tunneling is an effective method of ensuring secure network management and secure transmission of data over unsecured networks. By using SSH tunneling, organizations can enhance their security measures and operate efficiently. It is essential to follow best practices to ensure that SSH tunneling is used safely and efficiently.